Get started with Opsgenie as a user
Learn how to configure your profile, get notifications from Opsgenie and view on-call schedules.
Amazon CloudWatch Integration improves the usage of Amazon CloudTrail to filter events according to CloudWatch alarms. Therefore, instead of taking care of all trail events, more refined alerts are created.
When Amazon CloudTrail receives a new log, the log event is sent to Amazon CloudWatch Logs. CloudWatch monitors and evaluates trail events to filter important ones. When a CloudWatch alarm is triggered, an alert is created in Opsgenie automatically through the integration. To set up CloudWatch alarms, Amazon CloudFormation template is used.
Go to Settings > Integrations. Search for Amazon CloudTrail and select Add. (You don't have to configure SNS and CloudWatch alarms that are shown in this page, CloudFormation template will be used for configurations in this document.)
Specify who is notified of Amazon CloudTrail alerts using the Responders field. Auto-complete suggestions are provided as you type.
Select Save Integration.
1.From "Amazon CloudTrail Console" navigate to Trails. Click Create trail or use an existing one.
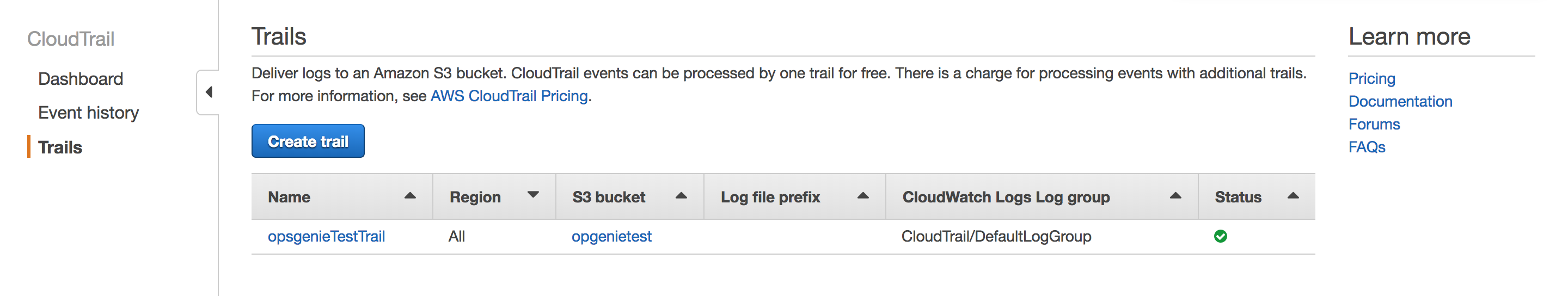
2. In "S3" tab, create a new S3 bucket or select an existing one. Then create trail. "SNS topic" is set in the CloudFormation template.
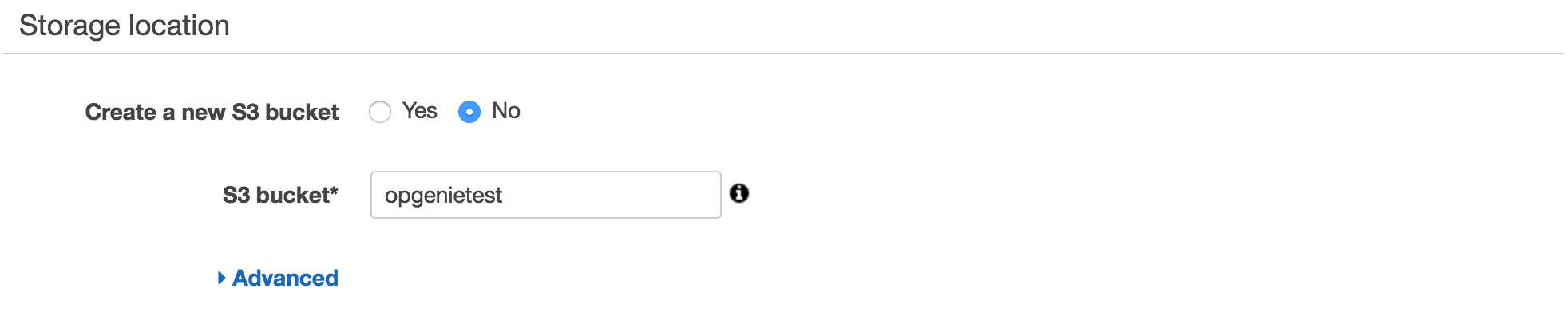
3. For "CloudWatch Logs", click Configure.
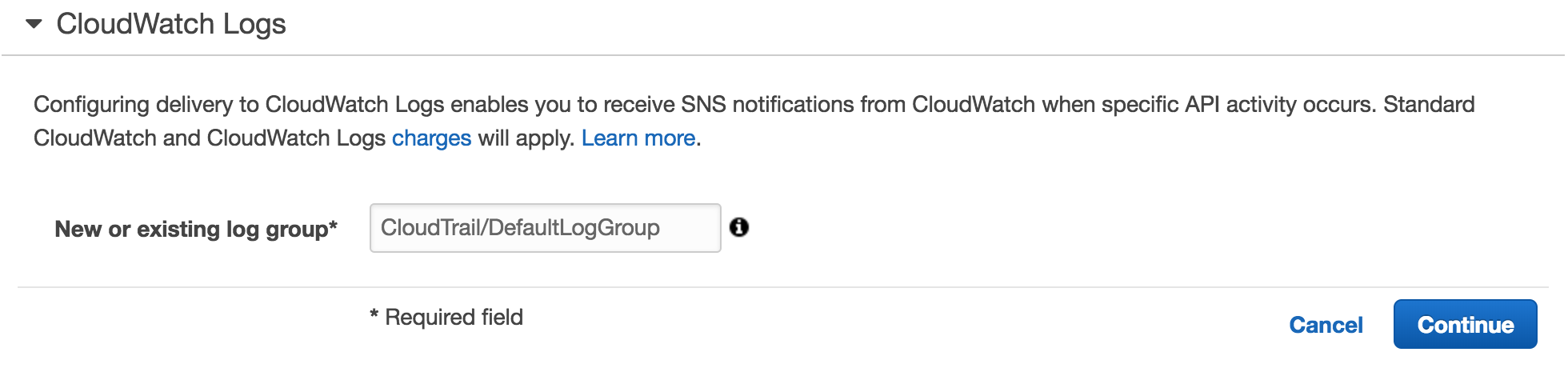
4. For "New or existing log group", type the log group name and then click Continue.
5. For the IAM role, choose an existing role or create one. Click Allow to grant CloudTrail permissions to create a CloudWatch Logs log stream and deliver events.
6. Download the CloudFormationtemplate: https://raw.githubusercontent.com/opsgenie/opsgenie-integration/master/cloudtrail/CloudWatch_Alarms_for_CloudTrail_API_Activity_OpsGenie.json
SNS topic and subscription, and CloudWatch alarms will be located at JSON file of CloudFormation template.
7. Open the AWS CloudFormation console and click Create Stack.
8. On the "Select Template" page, click Choose File, and then select the AWS CloudFormation template previously downloaded. Then click Next.
9. For Name, type a stack name. CloudWatchAlarmsForCloudTrailOpsgenie is used for the following example. "Endpoint" is the same with the integration endpoint created at the beginning of this document. For "LogGroupName", type the name of the log group specified when configuring the trail to deliver log files to CloudWatch Logs at 4. step. Click Next.
10. For "Options", create tags or configure other advanced options. These are not required. Click Next then click Create.
11. Check that the "CloudFormation" stack is created.
12. Navigate to the "CloudWatch" page and check that the alarms are visible.
13. Navigate to the "SNS" page and check that the topic is created and subscription is added.
The CloudFormation template that is used in this document contains some basic CloudWatch alarms to filter CloudTrail events such as Amazon S3 Bucket Events, Network Events, Amazon EC2 Events and CloudTrail and IAM Events. For further usage, modify the CloudFormation template.
JSON
1
2
3
4
5
6
7
8
9
10
11
12
{
"Type": "Notification",
"MessageId": "x59595a1-5f0b-5ea8-8ad8-c714d42a48d1",
"TopicArn": "arn:aws:sns:us-east-1:485823035610:CloudWatchAlarmsForCloudTrail-AlarmNotificationTopic-1OGWTWXTZ9W5X",
"Subject": "ALARM: \"CloudTrailChanges\" in US East (N. Virginia)",
"Message": "{\"AlarmName\":\"CloudTrailChanges\",\"AlarmDescription\":\"Alarms when an API call is made to create, update or delete a CloudTrail trail, or to start or stop logging to a trail.\",\"AWSAccountId\":\"825426534673\",\"NewStateValue\":\"ALARM\",\"NewStateReason\":\"Threshold Crossed: 1 datapoint [1.0 (03/07/18 14:18:00)] was greater than or equal to the threshold (1.0).\",\"StateChangeTime\":\"2018-07-03T14:23:28.949+0000\",\"Region\":\"US East (N. Virginia)\",\"OldStateValue\":\"INSUFFICIENT_DATA\",\"Trigger\":{\"MetricName\":\"CloudTrailEventCount\",\"Namespace\":\"CloudTrailMetrics\",\"StatisticType\":\"Statistic\",\"Statistic\":\"SUM\",\"Unit\":null,\"Dimensions\":[],\"Period\":300,\"EvaluationPeriods\":1,\"ComparisonOperator\":\"GreaterThanOrEqualToThreshold\",\"Threshold\":1.0,\"TreatMissingData\":\"\",\"EvaluateLowSampleCountPercentile\":\"\"}}",
"Timestamp": "2018-07-03T14:23:29.029Z",
"SignatureVersion": "1",
"Signature": "uzbpxna6ywOS1OSVhP24PDjXd/DCIPoU+D5jPI9U6BORcWIbnofUcyRqF5L/ssJ89kjuEgVxQjwxfLrrTReG38bx05g4WrNIPWfwxiWYV9G5GLW89h4lr3X/NgvXqvbx3QiA9UeeOgLcStXb19RXuX5Y3ckLHpbChKurWoxA+eBx19ce4ZO0w6jr66ZEEPoDOtWZ4Pplx5a4YdGKnWJA8Ostarx1dOziLIxSSzl6BFVEeUM8Fr07T34iIZx7IDn5Ln76muISG6BG2CeUcEExyXgizfHde/h/O2qqH2truxUnZ15Ez7/I9mHXDtikyBS4dL8B5dXWlIignuK12rk9rg==",
"SigningCertURL": "https://sns.us-east-1.amazonaws.com/SimpleNotificationService-eaea6120er6ea12e88dcd8bcb5dca752.pem",
"UnsubscribeURL": "https://sns.us-east-1.amazonaws.com/?Action=Unsubscribe&SubscriptionArn=arn:aws:sns:us-east-1:585416034660:CloudWatchAlarmsForCloudTrail-AlarmNotificationTopic-1OGWxWXTZ9W5B:c88cde98-cd5f-4f36-857c-8c92339c55d2"
}
This payload is parsed by Opsgenie as:
JSON
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
{
"AWSAccountId": "935426074681",
"TopicArn": "arn:aws:sns:us-east-1:785926035630:CloudWatchAlarmsForCloudTrail-AlarmNotificationTopic-1OGWTWXTZ9W5B",
"alertSource": "com.opsgenie.client.model.dto.ActionSourceCustomDto@35ae8359[domain=integration,sourceType=CloudWatch,sourceName=CloudWatch,incomingDataId=a2fde995-bd11-47d7-a5fa-bce4f94f5328,sourceSubName=Create Alert,customSourceName=<null>,actorUserId=<null>]",
"NewStateReason": "Threshold Crossed: 1 datapoint [1.0 (03/07/18 14:18:00)] was greater than or equal to the threshold (1.0).",
"NewStateValue": "ALARM",
"Subject": "ALARM: \"CloudTrailChanges\" in US East (N. Virginia)",
"StateChangeTime": "2018-07-03T14:23:28.949+0000",
"Type": "Notification",
"Trigger": "MetricName : CloudTrailEventCount\nNamespace : CloudTrailMetrics\nStatisticType : Statistic\nStatistic : SUM\nUnit : null\nDimensions : []\nPeriod : 300\nEvaluationPeriods : 1\nComparisonOperator : GreaterThanOrEqualToThreshold\nThreshold : 1.0\nTreatMissingData : \nEvaluateLowSampleCountPercentile :",
"AlarmDescription": "Alarms when an API call is made to create, update or delete a CloudTrail trail, or to start or stop logging to a trail.",
"AlarmName": "CloudTrailChanges",
"OldStateValue": "INSUFFICIENT_DATA",
"delayIfDoesNotExists": "true",
"Region": "US East (N. Virginia)"
}
Was this helpful?