Add people to Guard Detect
As an organization admin, you can add people who are not organization admins to Guard Detect by granting them the App admin role.
The User role is not currently in operation and does not grant access to anything.
Who can do this? |
Grant the product admin role to a user
The process for granting access is the same as granting admin permissions for other apps in your organization. Give users admin permissions
To grant the product admin role:
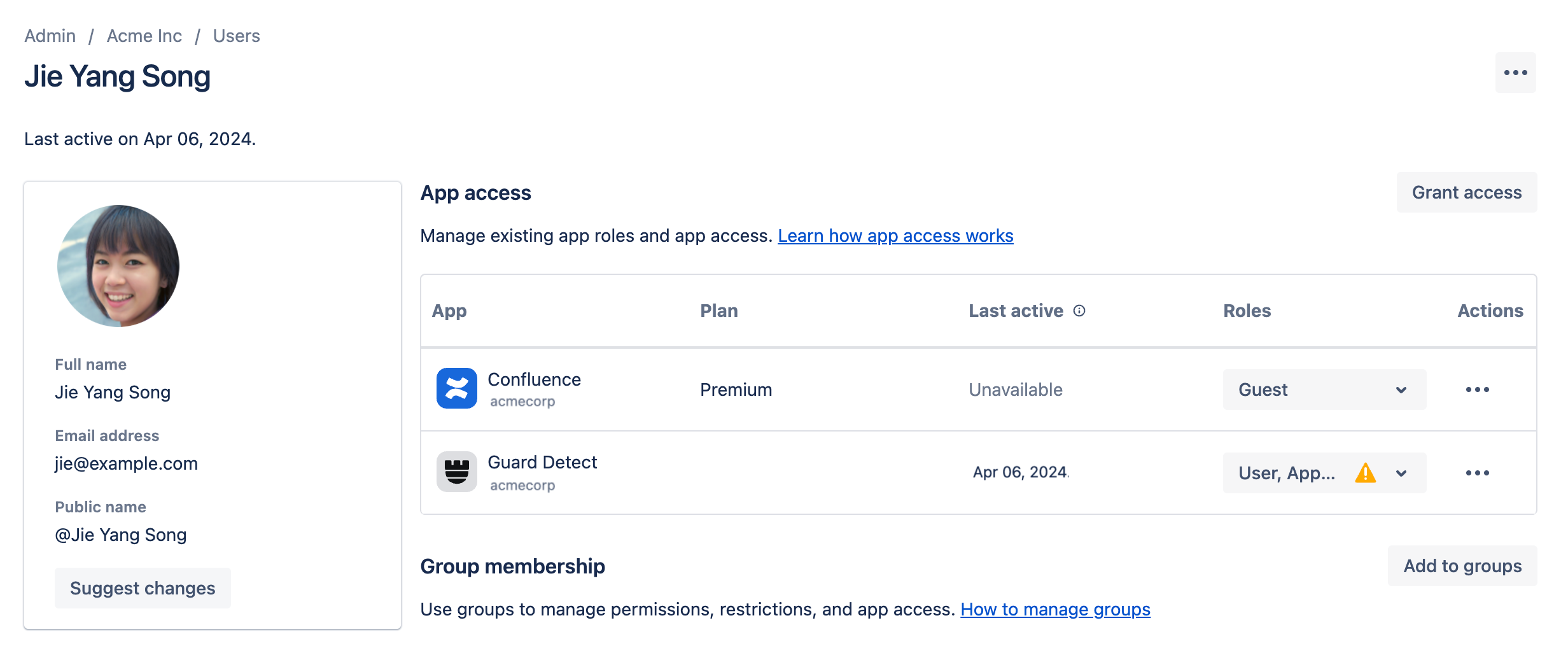
Go to Atlassian Administration. Select your organization if you have more than one.
Select Directory, then select Users.
Select a user.
Select Grant access and follow the prompts to grant the App admin role for Guard Detect.
This will add the user to the guard-detect-admins group.
Add a user to the admin group
You can also grant access by adding people to the guard-detect-admins group.
This method is useful if you need to add a lot of people or want to automatically add certain people when provisioning users from your identity provider. Understand default groups and permissions for each product
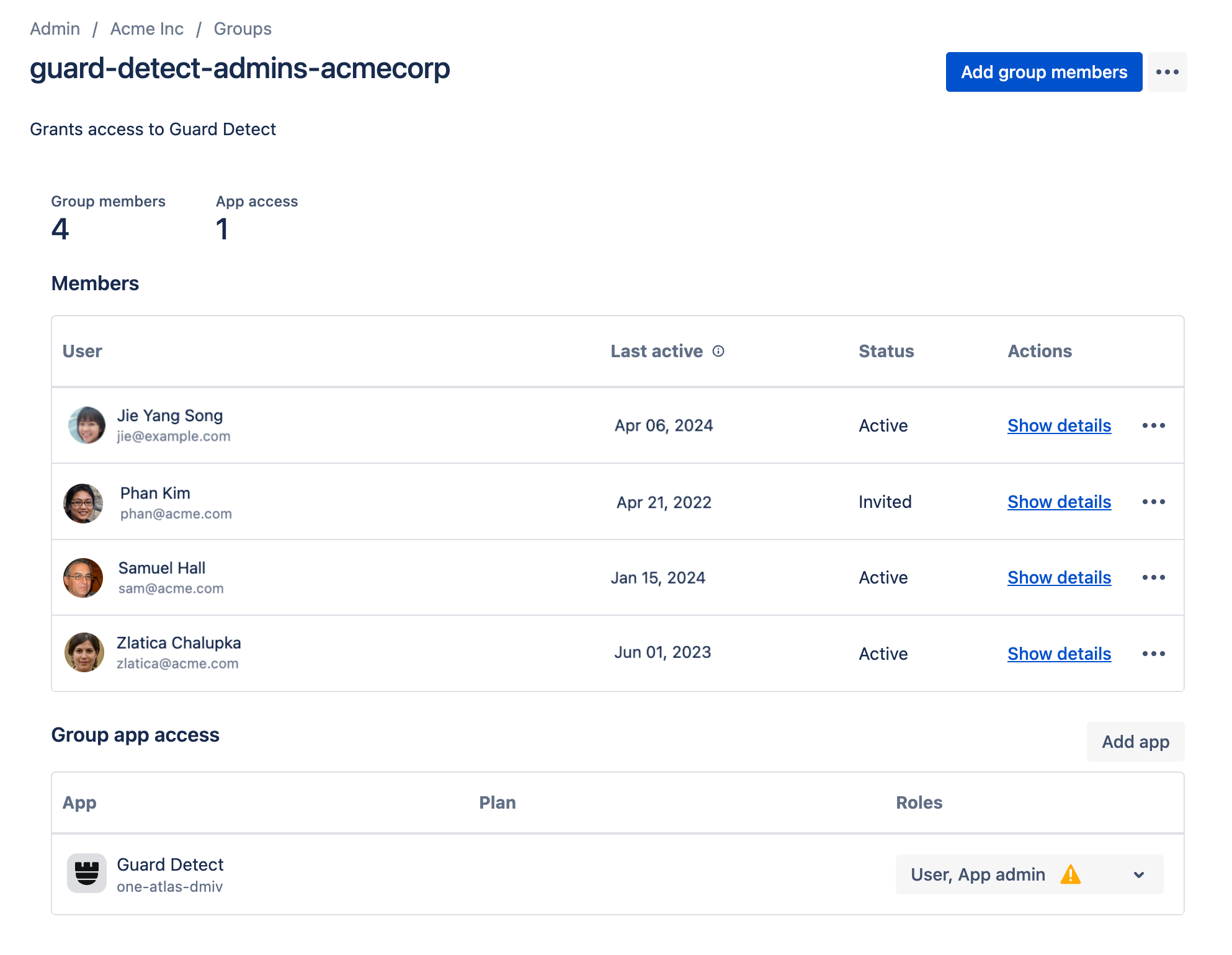
The guard-detect-users group is not currently in operation, and we don’t recommend using custom groups with Guard Detect at this time.
If your organization was part of the beta program (prior to May 2024), your groups will be named beacon-admins and beacon-users. These groups provide the same access and permissions as the guard-detect-users and guard-detect-admins, and are fine to continue using.
What information will a Guard Detect admin see?
In order to investigate an alert, we make certain data available so your team can act quickly. You should only grant Guard Detect access to people who have a need to access this data to do their job.
There are two places a Guard Detect admin can access data about the actor or subject:
in an alert
in the actor profile
We only surface information that is relevant to the investigation, such as:
Atlassian administration audit log events for that actor
Jira and Confluence app audit log events for that actor
User profile information including job title, app role, location.
User session information including IP address, login location, device operating system.
Certain activity data such as terms entered in the search field that match our list of suspicious search terms (they don’t see the full text of the actor’s search query)
Confluence space and page titles specifically related to the alert, regardless of whether the user has permission to see those spaces and pages. They won’t be able to see page or space content, just the title.
Jira project titles specifically related to the alert, regardless of whether the user has permission to see those projects. They won’t be able to see project content, just the title.
Text detected by a content scanning detection, including custom content scanning detections, regardless of whether the user has permission to see the page. They won’t be able to see the full content of the page, just the title and the sensitive data that was detected, with a few words either side for context.
Granting the app admin role for Guard Detect does not grant the person access to Atlassian administration features at admin.atlassian.com, or the ability to administer other apps, or view content they otherwise have no permissions to see.
Granting the app admin role for Guard Detect does grant the ability to turn off content scanning detections and create and edit custom content scanning detections.
What remediation actions can a Guard Detect admin take?
The remediation actions that a Guard Detect admin can do will depend on their other app permissions.
For example, they can’t suspend an actor or perform any action that requires the organization admin or app admin role unless they hold that role.
Was this helpful?