Learn about security solutions and standards
Care about security? We do too. Learn what Atlassian does and what you can do too.
Beacon is now Guard Detect, which is part of Atlassian Guard. Read the blog
Guard Detect is an intelligent threat detection system that actively monitors for suspicious activity and potentially sensitive data across your Atlassian organization. It alerts your team about critical events and configuration changes across your organization.
It helps you be the first to know about malicious users, compromised accounts, or genuine user mistakes that could leave your organization vulnerable. It gives security teams a head start to resolve issues before they become major incidents, and provides peace of mind that your security policies and best practices are being followed.
Guard Detect is part of your Atlassian Guard Premium subscription, and runs at the organization level. This means you don’t need to turn it on for particular sites or products. It detects suspicious user activity and potentially sensitive data in:
Atlassian Administration.
All Confluence product instances in your organization.
All Jira product instances in your organization.
Any Bitbucket workspaces linked to your organization.
Who can do this? |
We actively monitor for a range of issues, events and changes. The five main user activity categories are:
Data exfiltration events: including attempts to steal potentially sensitive data from your organization or share it externally which could indicate a potential data incident or insider threat.
Unusual user activity: giving you visibility into user activities that deviate from typical behavior, like excessive page crawling or suspicious search activity.
Authorization and access events: alerting you to policy or API key changes which could indicate an attempt to exploit vulnerabilities or gain unauthorized access to a system.
Integration change events: helping you track which third party apps have been granted access to your systems, and what type of access they have.
Product configuration change events: including insecure configurations or accidental configuration changes - like adding or removing org admins.
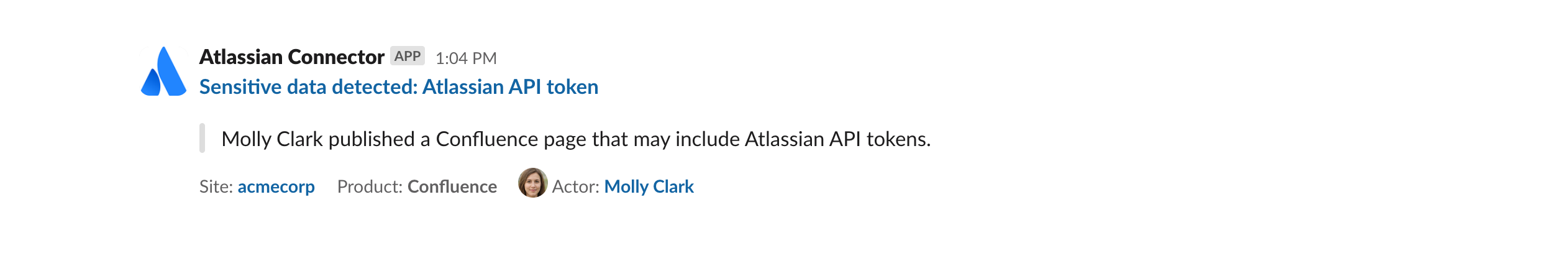
In addition to suspicious user activity, we also monitor for potentially sensitive text being added to Confluence pages and blogs, such as:
Financial: text that may contain credit card or bank account numbers or cryptocurrency addresses.
Credentials: text that may contain API tokens or private keys.
Identity: text that may contain US Social Security Numbers (SSN).
Custom: text that may contain terms that are sensitive to your organization.
To see the full range of detections available to your organization, go to Guard Detect and select Detections from the header.
We generate an alert in real-time when we detect suspicious user activity or potentially sensitive data. The alert list contains all recent alerts, making it easy for your team to react quickly.
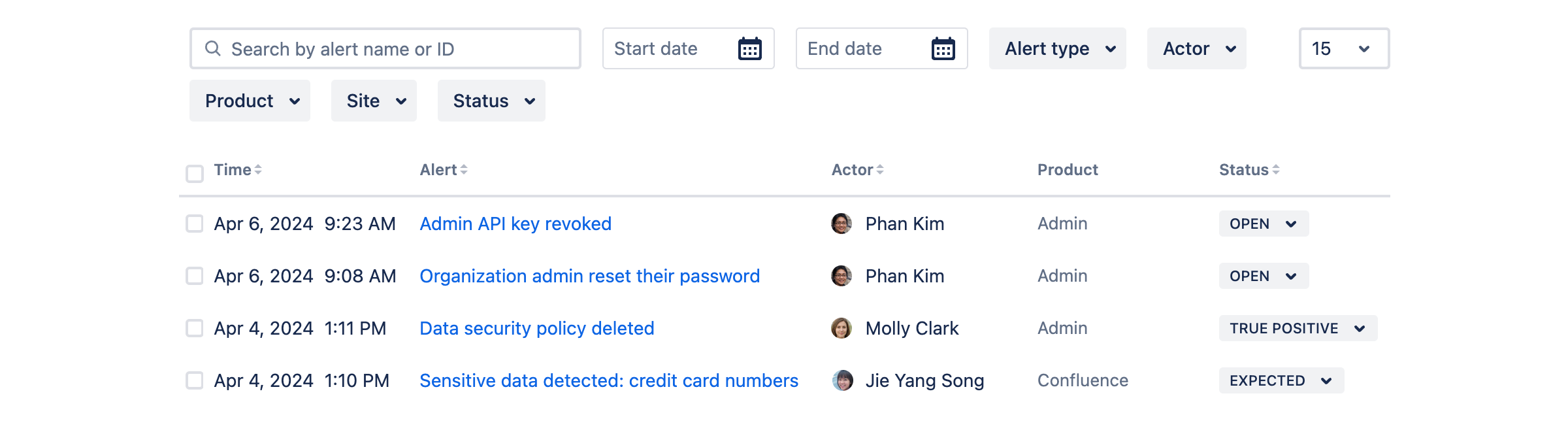
Each alert contains:
Information about the actor, the person who performed the activity that generated the alert.
Information about the subject of the alert, this might be the entity that was acted on, such as a page, or configuration, or may be a person.
Recommended investigation steps to help guide your admins and security team to more information to use when determining whether the alert is either suspicious, or expected behavior.
Recommended remediation steps and actionable links to help your admins and security team act quickly, such as suspending the actor or restoring a configuration.
The alert is designed to make it easy for the person investigating, providing contextual, and relevant information.
While you can view alerts in Guard Detect, you can also send alerts to just about any other system using webhooks. This is useful if you already use a Security information and event management (SIEM), Splunk, or other tool to monitor your organization.
Was this helpful?