Learn about security solutions and standards
Care about security? We do too. Learn what Atlassian does and what you can do too.
Connect an identity provider and configure single sign-on for your customers.
Who can do this? |
Don’t use this feature if you intend to provision and sync accounts for portal-only customers or users because this feature is designed to authenticate portal-only customers for Jira Service Management only.
You can provision and sync managed users and external users to your organization. Learn more about user provisioning
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, such as an identity provider and a service provider.
SAML for single sign-on (SSO) allows your customers to authenticate through your organization's identity provider when they log in to your Jira Service Management help center. Customers only need to log in one time to access multiple portals for one help center during an active session.
Customers outside your organization can only access your Jira Service Management help center. We don’t count these customers toward your subscription. Learn more about Jira Service Management customer accounts
You can set up single sign-on for internal customers (e.g. employee customers) with Atlassian accounts. Learn more about configuring SAML SSO with an identity provider for users in your organization
After you configure SAML single sign-on with your identity provider, you need to enable single sign-on through Jira settings for Jira Service Management. Learn more about authenticating your portal-only customers
Subscribe to Atlassian Guard Standard from your organization. Understand Atlassian Guard
Make sure you're an admin for an Atlassian organization.
Add an identity provider to Jira Service Management. How to add an identity provider for portal-only customers
Check that your Atlassian product and your identity provider use the HTTPS protocol to communicate and that the configured product base URL is the HTTPS one.
Make sure the clock on your identity provider server is synchronized with NTP. SAML authentication requests are only valid for a limited time.
Go to the Authentication page under your Jira settings to test the single sign-on experience before enabling SSO for all your portal-only customers. Learn more about testing single sign-on for customer login
Your SAML SSO setup depends on the identity provider. The Atlassian support team can help you with the setup instructions for supported identity providers.
You’re unable to use your identity provider’s pre-configured Atlassian Cloud applications or apps to configure SAML for portal-only customers. Apps are designed to work with SAML for Atlassian accounts.
The exact steps and terminology may vary depending on your specific identity provider, please refer to the provider’s documentation or support resources for detailed guidance if needed.
To integrate a generic application with your chosen identity provider:
Log in to your chosen identity provider account.
Look for the option to create your own application.
Once inside the application creation area, search for the option to integrate any other application not listed in the app gallery or library.
Select this option to proceed with the configuration process.
Identity provider | Provider’s set up instructions |
|---|---|
Active Directory Federation Services (AD FS) | |
Auth0 | |
CyberArk (Idaptive) | |
Google Cloud Identity | |
Microsoft Azure AD | |
Okta | |
OneLogin | |
PingFederate |
Which user management experience do you have?
To check, go to your organization at admin.atlassian.com and select Directory. If the Users and Groups lists are found here, then you are using the centralized user management. Learn more about the centralized user management
Original | Centralized |
As a site administrator or organization admin, Users is found under Product site. 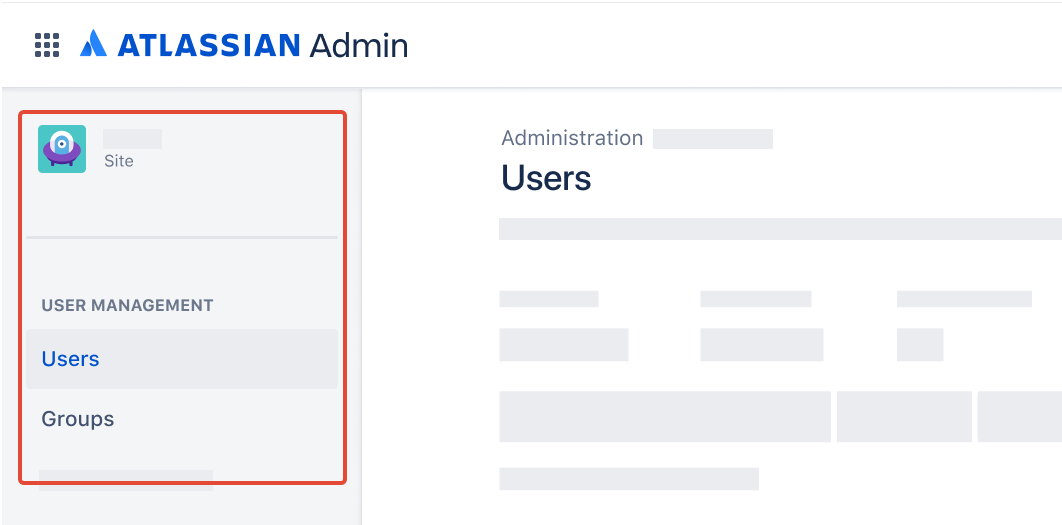 | As an organization admin, Users is found under Directory tab. 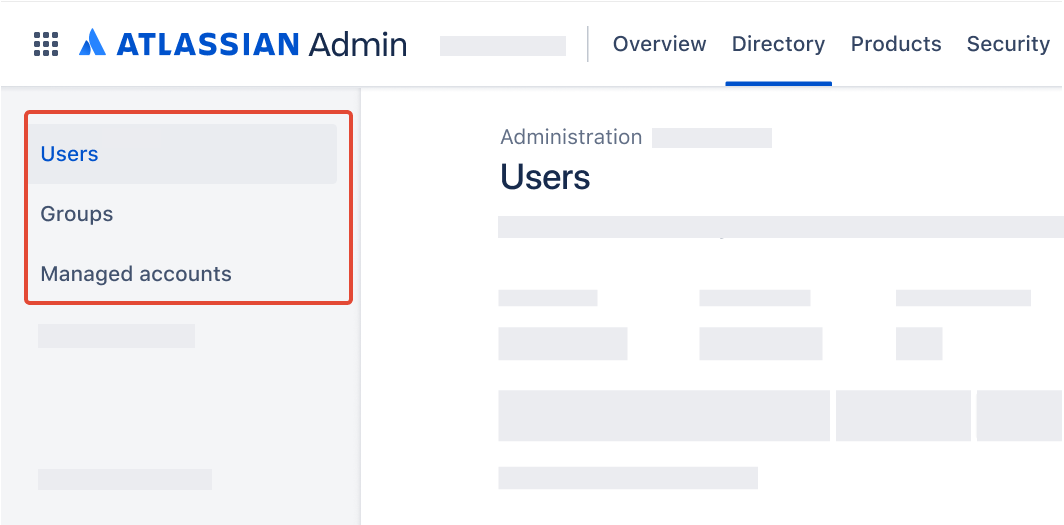 |
Jump to the
From your organization at admin.atlassian.com, select Products.
Under Sites and products, select the site you want to configure the SAML SSO for.
Under Jira Service Management, select Portal-only customers.
Select (more option) > Identity providers.
Select Set up SAML single sign-on.
Add SAML details.
Select Save.
SAML details | Description |
|---|---|
Identity provider Entity ID | This value is the URL for the identity provider where your product will accept authentication requests. |
Identity provider SSO URL | This value defines the URL your users will be redirected to when logging in. |
Public x509 Certificate | This value begins with '-----BEGIN CERTIFICATE-----'. This certificate contains the public key we'll use to verify that your identity provider has issued all received SAML authentication requests. |
Service provider entity URL
Service provider assertion consumer service URL
The exact steps and terminology may vary depending on your specific identity provider, please refer to their documentation or support resources for detailed guidance if needed.
To integrate a generic application with your chosen identity provider:
Log in to your chosen identity provider account.
Look for the option to create your own application.
Once inside the application creation area, search for the option to integrate any other application not listed in the app gallery or library.
Select this option to proceed with the configuration process.
Select Save in your identity provider.
When you set up your identity provider, these are your SAML attributes:
Instructions | SAML Attribute | Map to your identity provider |
|---|---|---|
Required | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname | User's first name |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname | User's last name | |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name, OR http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn | Internal Id for the user that will not change. Note that this Id should NOT be the user's email address. | |
Required | NameID | User’s email |
RelayState for identity provider (IDP) initiated SSO
If you need to configure an identity provider-initiated login flow, use the following relaystate URL:
<baseurl>/servicedesk/customer/portals
We recommend that you test and then enable single sign-on for your Jira Service Managementhelp center. When you enable single sign-on your customers can access your help center using their identity credentials with the identity provider. Learn more about authenticating your portal-only customers
Once you delete the SAML configuration, your customers won’t be able to authenticate from the identity provider. Instead, they will need to use their portal-only accounts (email and password) on your site to access your help center. If a customer doesn’t have a portal-only account password, we’ll ask them to set it up at the time they attempt to log in to your help center.
Before you delete the SAML single sign-on configured for your identity provider, make sure you have disabled single sign-on and enabled password authentication. Learn how to disable single sign-on and enable password
To delete SAML single sign-on configuration for an identity provider:
From your organization at admin.atlassian.com, select Products.
Under Sites and products, select the site you want to delete the SAML configuration for.
Under Jira Service Management, select Portal-only customers.
Select (more option) > Identity providers.
Select the directory you want to delete the SAML configuration.
Select View SAML configuration > Delete configuration.
When you delete the SAML configuration, you still have a subscription to Atlassian Guard Standard. If you want to unsubscribe, go to Unsubscribe from Atlassian Guard Standard.
Go to your site's Admin at admin.atlassian.com. If you're an admin for multiple sites or an organization admin, click the site's name and URL to open the Admin for that site.
Select Jira Service Management.
Select (more option) > Identity providers.
Select Set up SAML single sign-on.
Add SAML details.
Select Save.
SAML details | Description |
|---|---|
Identity provider Entity ID | This value is the URL for the identity provider where your product will accept authentication requests. |
Identity provider SSO URL | This value defines the URL your users will be redirected to when logging in. |
Public x509 Certificate | This value begins with '-----BEGIN CERTIFICATE-----'. This certificate contains the public key we'll use to verify that your identity provider has issued all received SAML authentication requests. |
Service provider entity URL
Service provider assertion consumer service URL
The exact steps and terminology may vary depending on your specific identity provider, please refer to their documentation or support resources for detailed guidance if needed.
To integrate a generic application with your chosen identity provider:
Log in to your chosen identity provider account.
Look for the option to create your own application.
Once inside the application creation area, search for the option to integrate any other application not listed in the app gallery or library.
Select this option to proceed with the configuration process.
Select Save in your identity provider.
When you set up your identity provider, these are your SAML attributes:
Instructions | SAML Attribute | Map to your identity provider |
|---|---|---|
Required | http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname | User's first name |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname | User's last name | |
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name, OR http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn | Internal Id for the user that will not change. Note that this Id should NOT be the user's email address. | |
Required | NameID | User’s email |
RelayState for identity provider (IDP) initiated SSO
If you need to configure an identity provider-initiated login flow, use the following relaystate URL:
<baseurl>/servicedesk/customer/portals
We recommend that you test and then enable single sign-on for your Jira Service Managementhelp center. When you enable single sign-on your customers can access your help center using their identity credentials with the identity provider. Learn more about authenticating your portal-only customers
Just-in-time provisioning is supported during both service provider-initiated and identity provider-initiated flows.
You need to be a Jira admin to enable single sign-on for your Jira Service Management site:
Go to the Jira settings > Products > Authentication. Learn more about configuring settings to authenticate your portal-only customers
Make sure that you have the option Enable single sign-on selected and saved.
Once these settings have been confirmed, a new customer will go to your help center URL https://INSTANCE.atlassian.net/servicedesk/customer/portals to just-in-time provision a portal-only account.
The service provider-initiated login experience in the help center will be:
The customer navigates to https://INSTANCE.atlassian.net/servicedesk/customer/portals
The customer enters their Email address and selects Continue.
The customer selects Continue with single sign-on and is redirected to their identity provider.
If the customer successfully authenticates against the identity provider (or has a cached session), we automatically create a portal-only customer account for them, and they're redirected back to the help center website that initiated the login.
Once you delete the SAML configuration, your customers won’t be able to authenticate from the identity provider. Instead, they will need to use their portal-only accounts (email and password) on your site to access your help center. If a customer doesn’t have a portal-only account password, we’ll ask them to set it up at the time they attempt to log in to your help center.
Before you delete the SAML single sign-on configured for your identity provider, make sure you have disabled single sign-on and enabled password authentication. Learn how to disable single sign-on and enable password
To delete SAML single sign-on configuration for an identity provider:
Go to your site's Admin at admin.atlassian.com. If you're an admin for multiple sites or an organization admin, click the site's name and URL to open the Admin for that site.
Select Jira Service Management.
Select (more option) > Identity providers.
Select the directory you want to delete the SAML configuration.
Select View SAML configuration > Delete configuration.
When you delete the SAML configuration, you still have a subscription to Atlassian Guard Standard. If you want to unsubscribe, go to Unsubscribe from Atlassian Guard Standard.
Was this helpful?