View an alert
We send an alert when certain user activity or potentially sensitive data is detected across your organization. The alert contains information about who performed the activity, what they did, and when and where they did it.
Depending on the third party integrations set up in your organization, you might view alerts in the Guard Detect alerts list, via a notification in a chat tool like Slack or Microsoft Teams, or in your SIEM or other tool.
Who can do this? |
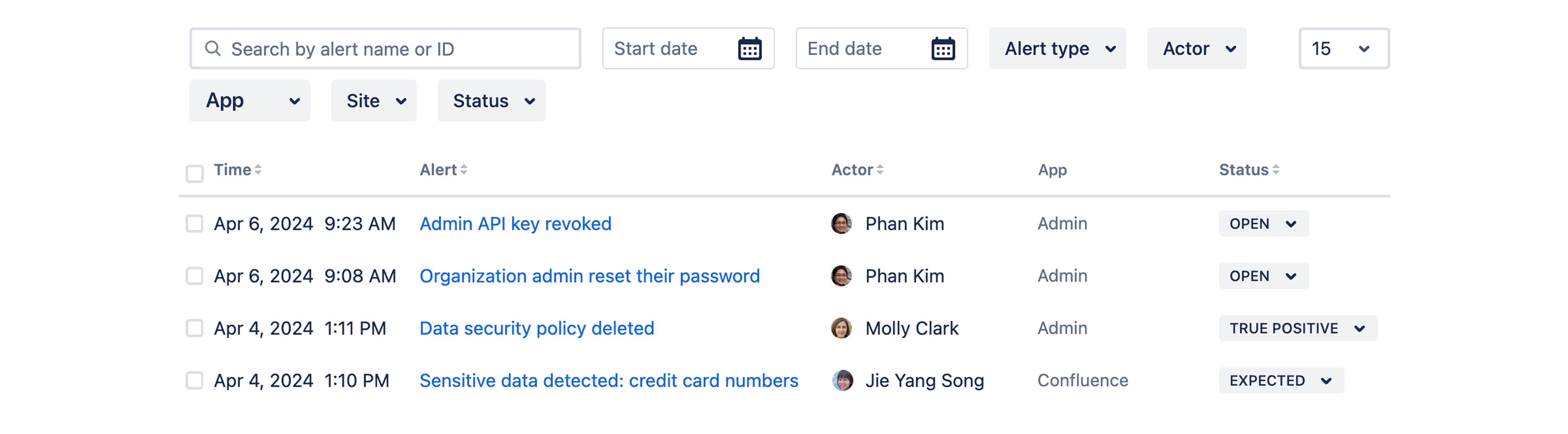
View the list of alerts
To view alerts:
In Guard Detect, go to Alerts in the header.
Select the alert you want to view.
Alerts are listed in chronological order. You can search by title or ID, or filter by event time, app, actor, the type of alert, and more.
Anatomy of an alert
Alerts are designed to surface the most important information so that you have everything you need to start your investigation. The data shown changes depending on what is most relevant to that alert type.
Here’s a summary of the information included in an alert. In this example we’ve used an alert generated by a content scanning detection.
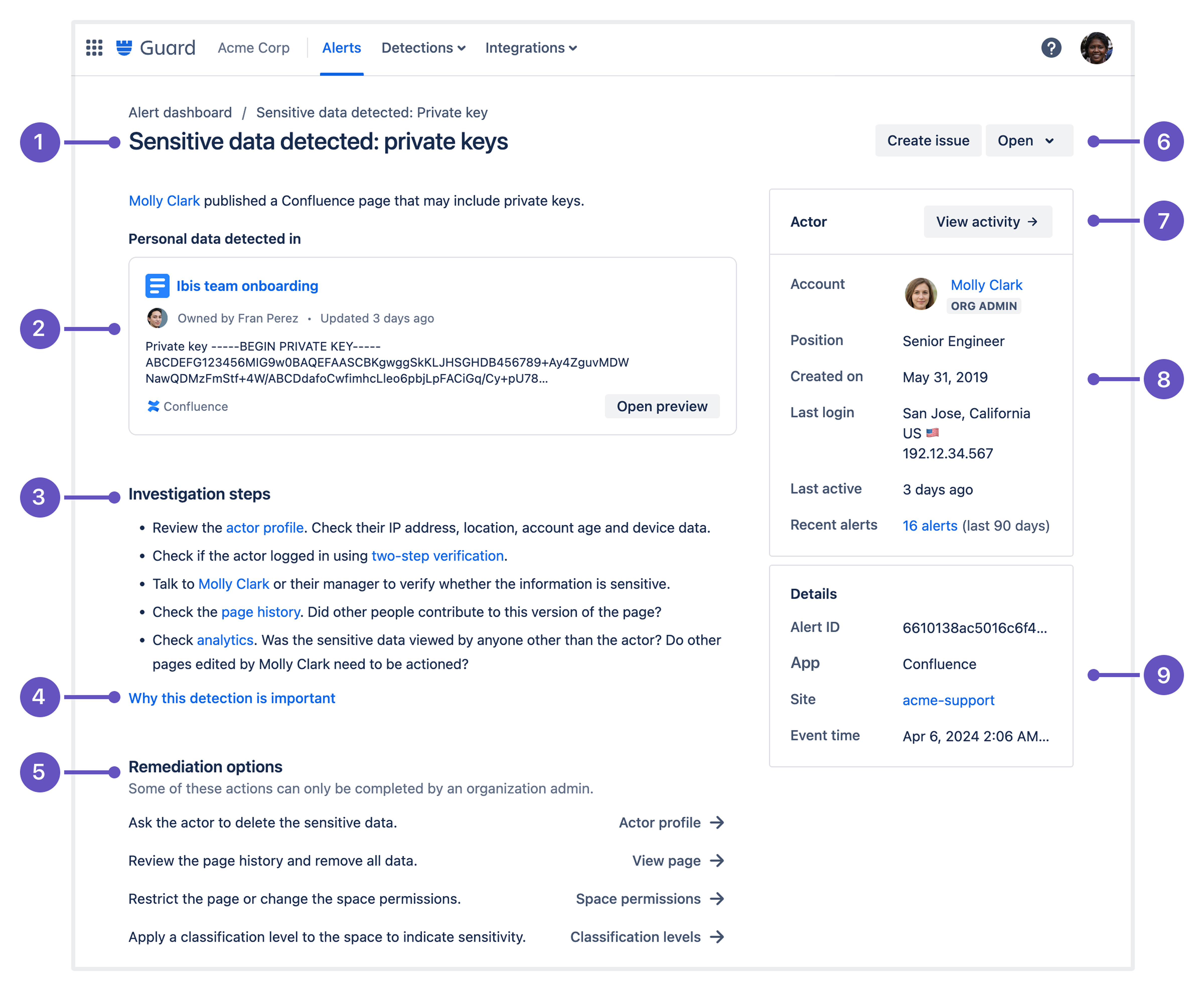
Alert title and description - high level summary that tells you who took the action, and what they did.
Preview or visualization - preview of the subject or additional data to help you understand the subject or context of the alert.
Recommended investigation steps - steps to help you gather more information and determine whether the alert is expected behavior or a threat.
Why its important - additional information to help you understand the threat that is being detected.
Recommended remediation options - quick access to common actions that may help you mitigate the risk or remediate the threat.
Alert status - mark the alert so your team knows the status of the investigation.
Actor activity - a timeline of the actor’s recent activity. Includes audit log events and alerts generated around the same time.
Actor summary - quick reference to the most important actor details. The actor name will take you to the actor profile with more detailed information.
Alert detail - additional context about the alert, and the site that the event happened in.
How long are alerts available?
Alerts remain in the alerts list for 180 days. Much of the alert data comes from the app and Atlassian Administration audit log data, so the retention periods for those logs will impact what data is available in an alert.
If you need to keep alerts for longer, consider using an integration to send alerts to a third party tool.
Was this helpful?