Send alerts to a SIEM or other tool
You can send alerts about suspicious activity or potentially sensitive data to any destination using webhooks. This is useful if you already use a Security information and event management system (SIEM) or other tool to monitor your organization.
Who can do this? |
Send alerts to a SIEM or other tool
You can use webhooks to send alerts to any destination, such as a SIEM, or an automation tool like Jira Automation, Zapier, or Workato.
Make sure you review the Atlassian guidance on webhooks to understand which ports are available and what information you’ll need to provide.
The ability to access organization-level data through the REST API differs between plan tiers. On Guard Premium, additional audit log actions and organization-level data are available via the API.
Check the documentation for your tool to find out how to create a webhook URL. This is where we’ll forward the alerts. To receive these alerts as email notifications, set up email workflows triggered by alerts sent via webhooks.
To send alerts to a SIEM or other tool:
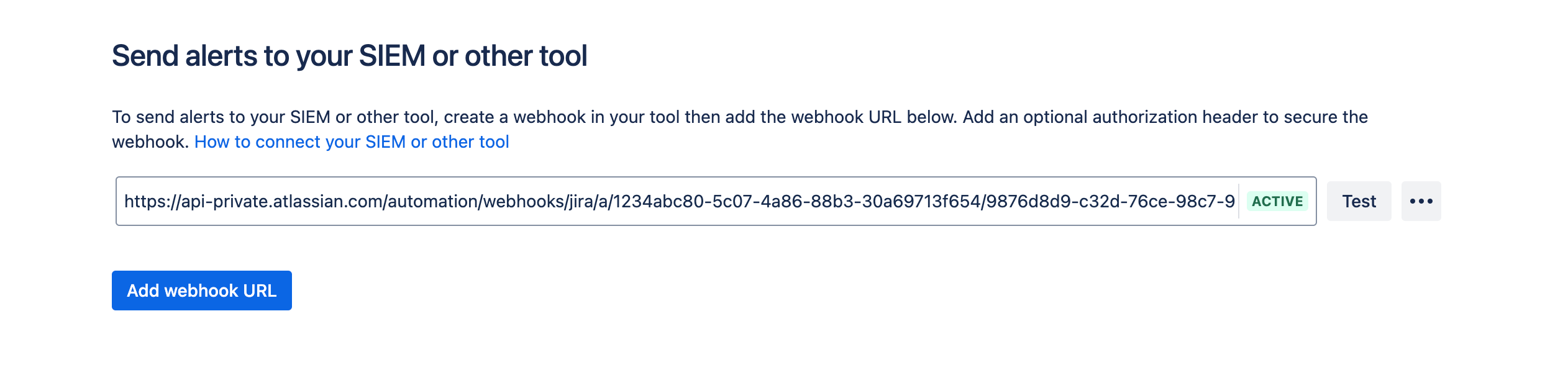
In Guard Detect, select Integrations, then SIEM webhooks.
Select Add webhook URL.
Enter the Webhook URL, and select Save.
Secure your webhook
You can secure the webhook connection by adding an authorization header.
In Guard Detect, select Integrations, then SIEM webhooks.
Select More actions (), then Add authorization header beside the webhook you want to secure.
Enter credentials using the <auth-scheme> <authorization-parameters> format. For example,
Basic <credentials>orBearer <token>.
This will be included in the header of every request.
What data is sent to your tool?
It’s important to know that once you set up an integration you will be sending alert data to the third party tool of your choosing. We send the alert title, description, and context which can include:
The name of the actor and their profile picture
The name of the subject, which can be a person or an entity (such as a space, project, or policy)
The site URL or page URL where the activity happened.
We respect the visibility settings in the actor’s Atlassian Account profile. If the actor has chosen not to share their profile picture with their Atlassian organization, we respect that setting.
You should make sure that it’s appropriate for this data to be shared with your third party tool before setting up the integration.
Was this helpful?