OpenID Connect authentication fails with "Exchanging authorization tokens failed"
Platform Notice: Data Center Only - This article only applies to Atlassian apps on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
After enabling OpenID Connect (OIDC) for a Jira environment, the user is redirected to the IdP and enter their credentials.
However, the login fails and the user is prompted with the Jira login screen again.
Environment
Jira DC 8.6+ (or Jira Server with a DC license)
The SSO for Atlassian Server and Data Center app on version 4.0.1+ (with support for OIDC)
Diagnosis
The Jira server logs show the following exception:
2020-11-13 14:48:59,153+0100 http-nio-8080-exec-24 url:/jira/plugins/servlet/oidc/callback ERROR anonymous 888x315970x1 uz0qod 53.61.238.57,53.31.55.76 /plugins/servlet/oidc/callback [c.a.p.a.i.web.filter.ErrorHandlingFilter] Exchanging authorization tokens failed.
com.atlassian.plugins.authentication.impl.web.usercontext.AuthenticationFailedException: Exchanging authorization tokens failed.
at com.atlassian.plugins.authentication.impl.web.oidc.OidcConsumerServlet.exchangeAuthorizationCodeForTokens(OidcConsumerServlet.java:196)
at com.atlassian.plugins.authentication.impl.web.oidc.OidcConsumerServlet.getOidcTokens(OidcConsumerServlet.java:163)
at com.atlassian.plugins.authentication.impl.web.oidc.OidcConsumerServlet.doGet(OidcConsumerServlet.java:117)If you scroll down, you will see the exception cause logged. Here's an example of a 403 returned by an outbound proxy:
Caused by: java.io.IOException: Unable to tunnel through proxy. Proxy returns "HTTP/1.1 403 Forbidden"Cause
Unlike SAML which is purely browser-based, the OpenID authentication flow requires server-to-server communication to exchange authorization tokens. This happens at step 7 of the diagram below:
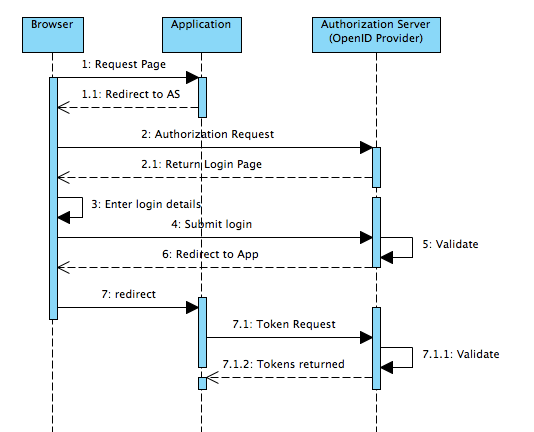
For the authentication to work, the Jira server/node must be able to reach the IdP. The error will occur if connectivity can't be established.
If the cause of the connectivity failure is proxy-related, it suggests that the outbound proxy used by Jira either doesn't allow connectivity or doesn't have an exception for the IdP host via the -Dhttp.nonProxyHosts JVM argument.
Solution
Either allow server-to-server connectivity between Jira and the IdP or, if you're using an outbound proxy, add an exception for the IdP host.
In a DC environment, the change has to be done on all nodes.
With proxy exceptions, you may run into the issue described in Jira server ignores http.nonProxyHosts JVM option.
Was this helpful?