FIDO2 based SSH keys (ecdsa-sk and ed25519-sk) don't work in Bitbucket Data Center
Platform Notice: Data Center Only - This article only applies to Atlassian apps on the Data Center platform.
Note that this KB was created for the Data Center version of the product. Data Center KBs for non-Data-Center-specific features may also work for Server versions of the product, however they have not been tested. Support for Server* products ended on February 15th 2024. If you are running a Server product, you can visit the Atlassian Server end of support announcement to review your migration options.
*Except Fisheye and Crucible
Summary
The FIDO2-enabled keys ecdsa-sk and ed25519-sk use the hardware authenticator (i.e. YubiKey) to provide an additional level of security for SSH, confirming the user presence at the time of use.
Generic support for FIDO2 keys was introduced in Bitbucket Data Center 8.13 and the ability to sign commits with an FIDO2 ssh key was introduced in Bitbucket Data Center 8.15.
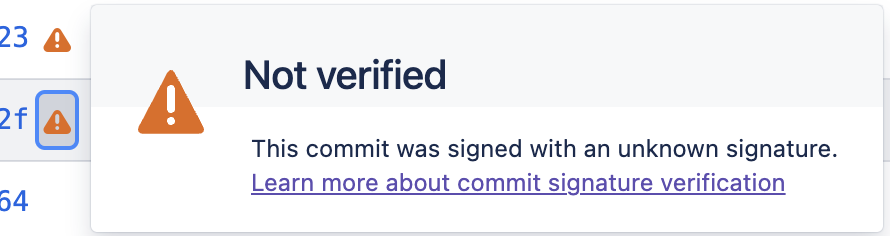
In some cases, the key generated according to instructions from Yubi's KB (https://developers.yubico.com/SSH/Securing_SSH_with_FIDO2.html) fails to authenticate for git operations.
Furthermore, the commits signed with this key, while successfully verifiable locally, show an unknown signature when pushed to Bitbucket.
Environment
Bitbucket Data Center
8.13 and newer for SSH authentication
8.15 and newer for SSH signature of commits
Diagnosis
Your key has been generated with the following command:
ssh-keygen -t ed25519-sk -O resident -O verify-required -C "Your Comment"And not with recommended in the documentation Creating SSH keys
ssh-keygen -t ed25519-sk -C <your-email>Cause
The root cause is in Open Source library https://github.com/apache/mina-sshd. The current implementation of the library doesn't support any flags on the SSH keys like PIN verification -O verify-required resulting into returning false to the verification request due to unrecognised flag. So that Bitbucket refuses the authentication and shows the signature is unknown because it can't recognize the key.
Solution
Generate the key without extra flags as recommended in Creating SSH keys:
ssh-keygen -t ed25519-sk -C <your-email>Was this helpful?